TAMUctf 18 Writeup
I participated in TAMUctf 18 (138th out of 1272) as Harekaze.
[Intro 1] Howdy!
Paste the flag from problem.
Flag: gigem{Howdy!}
[Misc 20] breadsticks 2
Download the problem file(breadSticks.bin).
I checked file breadSticks.bin and it seems like Microsoft OOXML.
mv breadSticks.bin breadSticks.docx
Open the breadSticks.docx.
Flag: ICanRead!
[Misc 25] you can run, you can hide
find the hidden flag. `ssh tamuctf@shell1.ctf.tamu.edu -p 2223` password: tamuctf
- Solution
find the flag by ls -aR
tamuctf@6cb21f6960f0:~$ cat .secret/.dont_delete_me.txt
gigem{TAMU_secret_society_qSD358OUYGcezTlFbqeh}
Flag: gigem{TAMU_secret_society_qSD358OUYGcezTlFbqeh}
[Crypto 25] Image`n That
Read the flag from given bmp image using stegno tool.
Flag: GIGEM{THE_WORLD_IS_IN_THE_EYE_OF_THE_BEHOLDER}
[Web 20] Reading
- Problem
I just love reading! http://web1.ctf.tamu.edu
- Solution
There are many words(flags) in this source(index.html).
Find the flag by tools.
(This case, I used grep command.)
Save index.html by curl http://web1.ctf.tamu.edu/
Find the flag by grep (I recommend you to use regular expressions to narrow the string.)
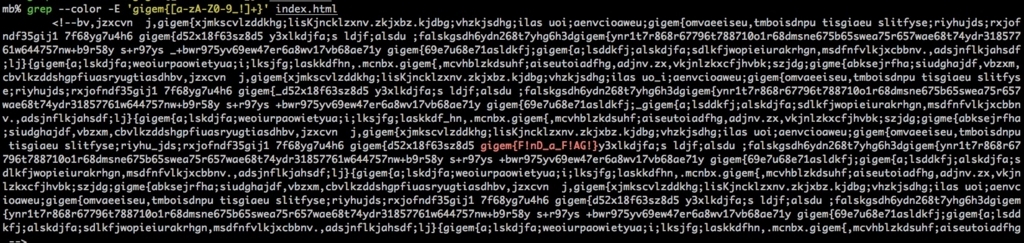
Flag: gigem{F!nD_a_F!AG!}
{Web 40} Bender
- Solution
Access the problem page.
No Google Bot can help you now!
View the robots.txt.
http://web3.ctf.tamu.edu/robots.txt
User-agent: * Disallow: oiuwerljk.html
Get the flag from here.
http://web3.ctf.tamu.edu/oiuwerljk.html
Flag: gigem{craw1ing_bot$!}
[Web 50] Bubbles
- Problem
I don't like taking baths. http://web4.ctf.tamu.edu
- Solution

Page title is SQLi and there is a form for submit.
Input ' or 1;# to Password form.
Flag: gigem{ScRuB7h3InpU7}
HarekazeCTF2018 Lost_data
Here is HarekazeCTF-2018-problem(with writeup) that I authored.
What is HarekazeCTF2018?
Problem Name: Lost_data
Problem file: lost_data.zip
- Points 100, Genre For + Misc, Author hiww, Solves 54.
Description Guess or try xxxxx in flag and replace to the correct word. xxxxx is uppercase. No need decipher the password of xxxxx.zip. lost_data.zip Hint: Refer the file contents of xxxxx.zip. filesystem is answer. (For + Misc, 100 points)
Solution(Writeup):
Step-1.(Recover QR-code from data.zip)
- Unzip the data.zip.
- The first 4 bytes of each file is
89 2E 2E 2E. - Even if using the file command the extension is unknown.
- But, there are some hint in the files[1..3].
- For example,
49 44 41 54in hex andIDATin ascii. - Replace the first 4 bytes to
89 50 4E 47. - The lost data was PNG.
- Scan QR-code by QR-code-scanner(e.g. zbarimg, iOScamera and human).
- The first 4 bytes of each file is
QR-code: HarekazeCTF{Y0u_G0t_FuNNy_F1ag_?DF?_T?_is_xxxxx}- Unzip the data.zip.
Step-2.(Investigate the xxxxx.zip)
By the way, have you ever used SD cards that can not add new files?
The filesystem have some restrictions.
You can know some information by unzip the xxxxx.zip(without password).
- The contents of xxxxx.zip seems to be fatxxx(file-size is 0KB).
- Total file number(
512) means filesystem's number of files limit. - Total number of files = Number of files limit in root directory of FAT16.
- This is why that
FAT16is correct answer of xxxxx.
Answer(FLAG):
HarekazeCTF{Y0u_G0t_FuNNy_F1ag_?DF?_T?_is_FAT16}
Addition:
- You can check your filesystem using
df -T.
- You can check your filesystem using
Reference: https://support.microsoft.com/ja-jp/help/436213
Github repository:
InCTF2017 Writeup
チーム Harekaze で InCTF 2017 に参加しました。順位は5位/ 156位でした。
[Forensics 50] EasyOne
問題でchal.imgというファイルが与えられる。
中にpassword.wavがあり、波形でPasswordが書かれていた。
(目が疲れるのでやめてほしい)
以下Password。
thisisthepasswordtoolongtobruteforce
次に、与えられたflag.zipを手に入れたパスワードで解凍する。 ※Mac標準のArchiverだとパスワードの入力ができなかったのでサードパーティ製のツールを用いた。
その後、中にflag.txtがあった。
ctf% ll && cat flag.txt
total 8
-rw-r--r--@ 1 ctf staff 34 12 14 21:08 flag.txt
inctf{th1s_1s_pr3tty_3asy_w4rmup}